Most IT departments are now heavily involved with vendor evaluations and lifecycle management of security equipment. Join us to learn more about how this mindset is changing and vendor due diligence is more important than ever.
What is the Lifecycle Of Electronic Security Equipment?
Financial institutions have a history of installing the latest security equipment for new construction or remodeled administrative facilities or branches. Many lack a strategy for maintaining the equipment or an end-of-life replacement strategy. This approach is not ideal for maintaining consistent quality or performance over time. The lifecycle of electronic security equipment is typically five years. The need for maintenance increases throughout the life of the equipment and quality decreases over time. Keeping equipment active beyond the end-of-life timeframe significantly decreases the quality of protection afforded by the equipment. A common symptom of equipment beyond end-of-life includes video images not effective at identifying suspects due to decreased image quality. Another common symptom is failure of the equipment at a time of critical need, such as during a bank robbery, or fraudulent transaction.
Electronic Security Equipment as Technology Assets
Financial institutions have transitioned or are in the process of transitioning from analog to IP-based electronic security equipment. IP-based security equipment is an immense step forward in functionality, integration capability, and quality. IP-based equipment connected to the financial institution’s network must be managed much differently than outdated analog equipment. IP-based security equipment must be patched, firmware updated, and penetration tested to verify cyber hardening is effective to prevent malware or hacking. A major trend is to treat IP-based security equipment as information technology assets and manage them just like servers, desktops, and laptop personal computers. Lifecycle replacement of security equipment is needed for the same reason lifecycle replacement occurs with laptops and smartphones. Technology assets at some point are no longer functional. Can you imagine trying to complete daily work on a ten-year-old smartphone or laptop? Equipment beyond end-of-life presents the following challenges:
- Are the devices capable of encryption?
- Can you patch the operating systems and is the firmware still supported by the manufacturer?
- Does the storage capability of video system allow for
90 days of stored images? - Can the video, access control, and alarm systems be integrated versus just operating independently?
- Are the systems capable of incorporating artificial intelligence and camera analytics?
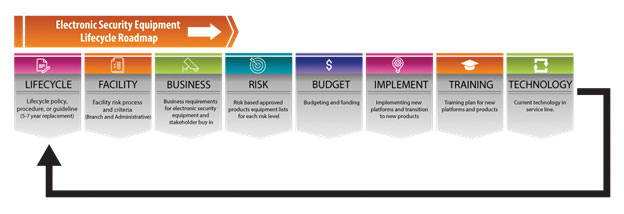
Developing an Electronic Security Equipment Lifecycle Roadmap and Program
Another trend is the partnership between facilities, security, and information technology to collaborate on the development of electronic security equipment business requirements. The business requirements drive the selection of equipment for acquisition by the financial institution. Including lifecycle replacement program planning into the process adds tremendous value and efficiency. Begin by developing an equipment database by location. The equipment database will help to determine where existing equipment, based on the age of the equipment, fits into the equipment lifecycle. The database should include the equipment manufacturer, the number of security equipment components, location inside or outside the facility, install date of the equipment, and the vendor that completed the installation. The database also allows you to perform annual analysis ahead of the budget cycle to plan for the consistent replacement of equipment that has reached the end of life. If your financial institution plans multiple years ahead, the database provides the information necessary to project annual budgets years in advance. One of the best ways to gather information for populating the database is to have your contracted service vendors complete an equipment questionnaire when they perform annual preventative maintenance. This approach reduces the costs of time and travel.
The next step is to determine the lifecycle of each component. A common target is five years for electronic security equipment. Some financial institutions may choose to integrate branch or administrative facility risk into the end-of-life decision criteria. An example would be higher-risk facilities — data centers, cash vaults, and branches with higher crime history — that are first in line to receive end-of-life replacements at five years.
Another component of the lifecycle program is a list of approved electronic security products that meet or exceed the financial institution’s cyber standards in addition to the business requirements. A semi-annual or at least annual review of your approved products is recommended to make sure you are spending available electronic security equipment budget dollars on equipment that performs to your standards for the present and future. If a component or components no longer perform to standards and updates are not readily available, it is time to find a different product that does meet or exceed your standards, rather than adopt a constant “like-for-like” or a complete system “rip and replace” all equipment strategy. The lifecycle replacement process enables financial institutions to infuse their security systems annually with current components as older equipment reaches end-of-life.
One emerging method of managing your electronic security equipment lifecycle program is an alternative to the typical purchase and five-year depreciation ownership model. For a smaller up-front cost and fixed monthly fee, there are trusted vendors that supply electronic security equipment that meets or exceeds your business and cyber standards for as long as you keep the agreement in place. Increasingly, organizations have found that equipment ownership is no longer an effective strategy for them, based on the value of the equipment at end-of-life and ever-advancing technology offering new features faster than ever before.
Electronic Security Equipment Can Do More
Keeping electronic security equipment refreshed at end-of-life, cyber protected, and high performing is not easy. Funding for electronic security equipment competes with all other financial institution expenditures. Traditional customer-facing systems are often prioritized over electronic security equipment in the competition for limited funds. Others may view electronic security equipment as customer-facing based on the protection these systems provide members and employees. Modern electronic security equipment can do much more than in the past. Camera analytics such as heat mapping can monitor member activity within public areas of the branch for marketing and customer experience analysis. A robust lifecycle replacement program can benefit your financial institution by maintaining equipment that protects the traditional methods and adds additional value in non-traditional ways as technology continues to rapidly evolve.










